The Five Eyes Intelligence Alliance, often referred to as simply “Five Eyes,” is a secretive international intelligence coalition comprising five English-speaking countries.
Established in the aftermath of World War II, this alliance has played a pivotal role in shaping global intelligence and security strategies. In this article, we will delve into the history, purpose, and controversies surrounding the Five Eyes alliance.
1. Origins and Formation:
The Five Eyes alliance originated as a post-war intelligence-sharing agreement between the United States, the United Kingdom, Canada, Australia, and New Zealand. Formed in 1946, its primary objective was to share signals intelligence (SIGINT) to counter the emerging Soviet threat during the Cold War.
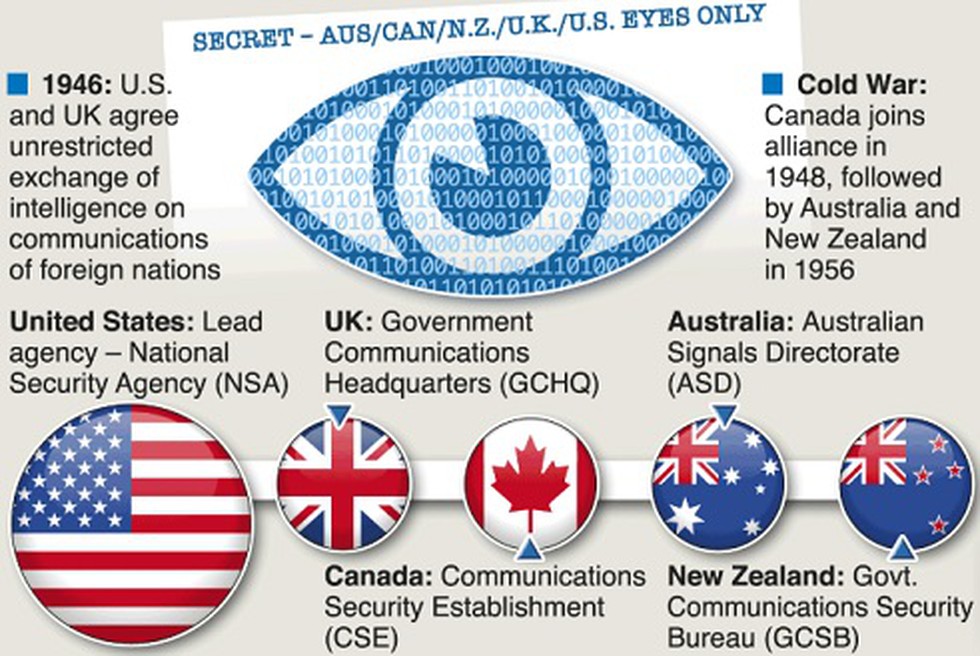
2. Intelligence Sharing:
One of the core functions of the Five Eyes alliance is the sharing of intelligence data, particularly in the fields of communications interception and codebreaking. Member countries pool their resources and expertise to monitor and analyze global communications, giving them a significant edge in understanding international developments.
3. Expanding Capabilities:
Over time, the alliance has expanded its focus beyond the Cold War era. It now encompasses various aspects of intelligence, including cybersecurity, counterterrorism, and economic espionage, reflecting the evolving nature of global threats.
4. Controversies and Concerns:
The Five Eyes alliance has faced criticism for its secretive operations, with concerns raised about potential violations of privacy and civil liberties. Revelations by whistleblowers like Edward Snowden shed light on the alliance’s extensive surveillance programs, raising questions about the balance between national security and individual rights.
5. Modern Challenges:
In the digital age, the Five Eyes alliance faces new challenges related to encryption, cybersecurity, and the proliferation of information. These challenges have prompted discussions on how to adapt and remain effective in a rapidly changing world.








Leave a Comment